One Of The Best Info About How To Handle Denial Of Service
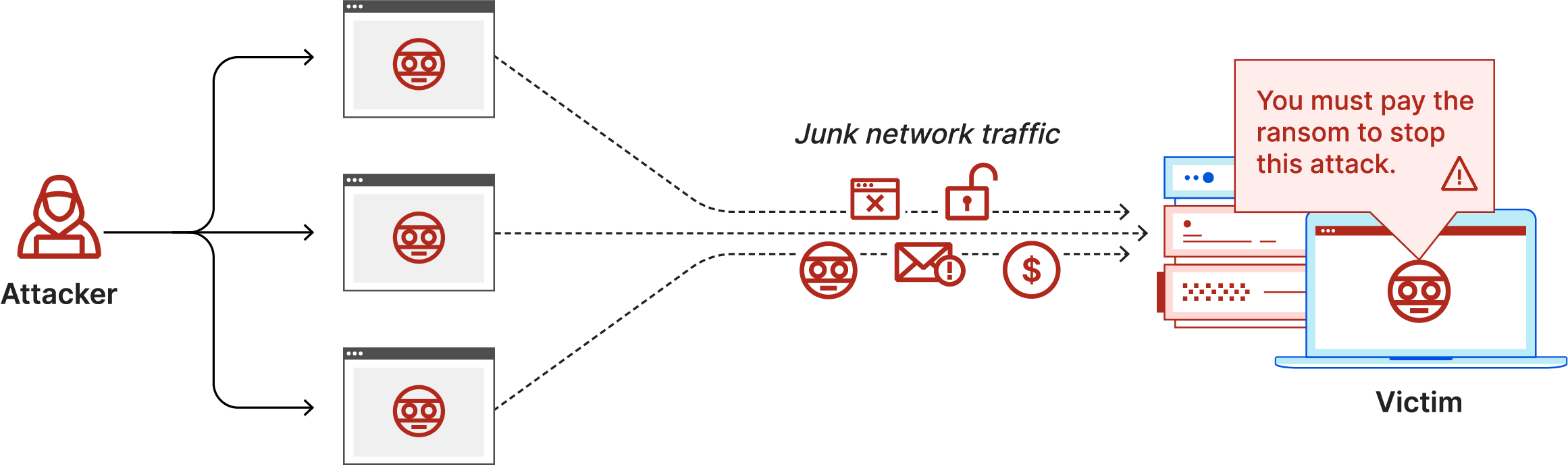
If ddos attacks are constant, customers will learn to take their money to another.
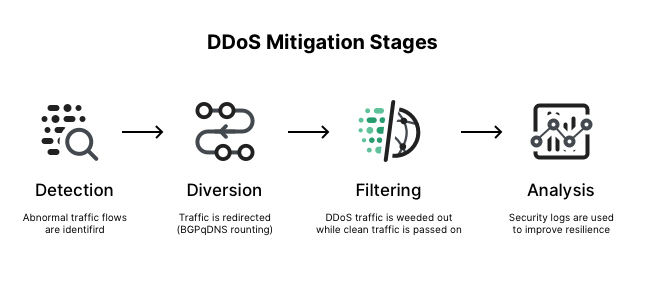
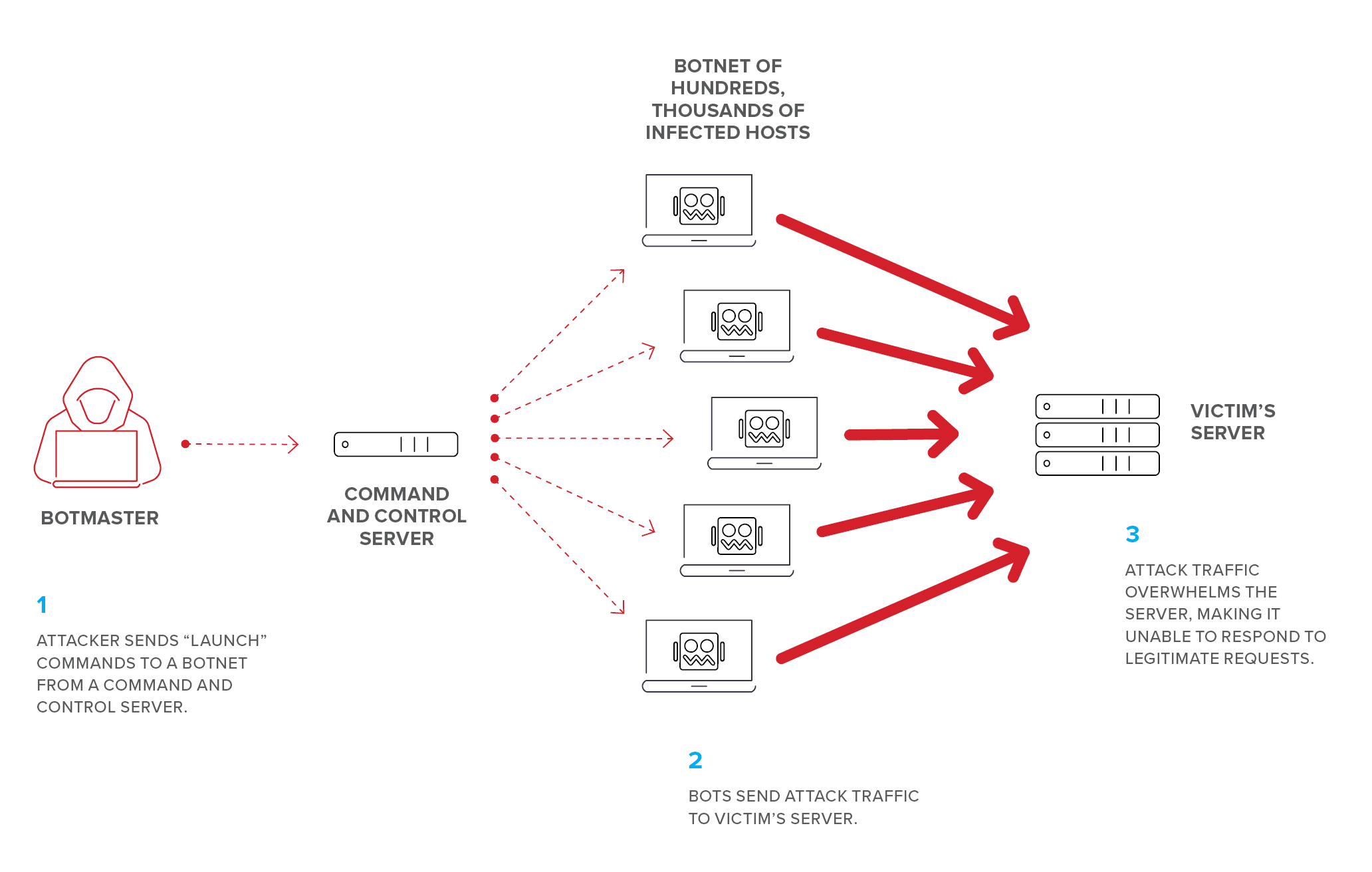
How to handle denial of service. Attempt to throttle or block ddos traffic as close to the network’s “cloud” as. While it is very difficult to fully block ddos attacks, you may be able to mitigate their effects. Reduce the number of combinations.
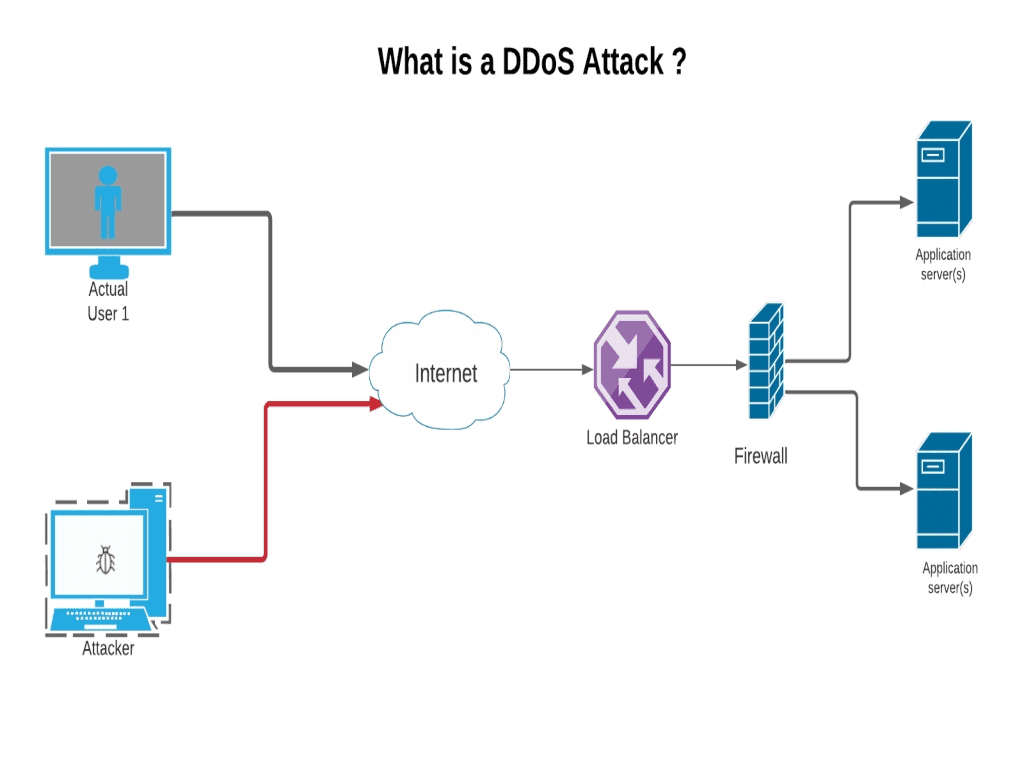
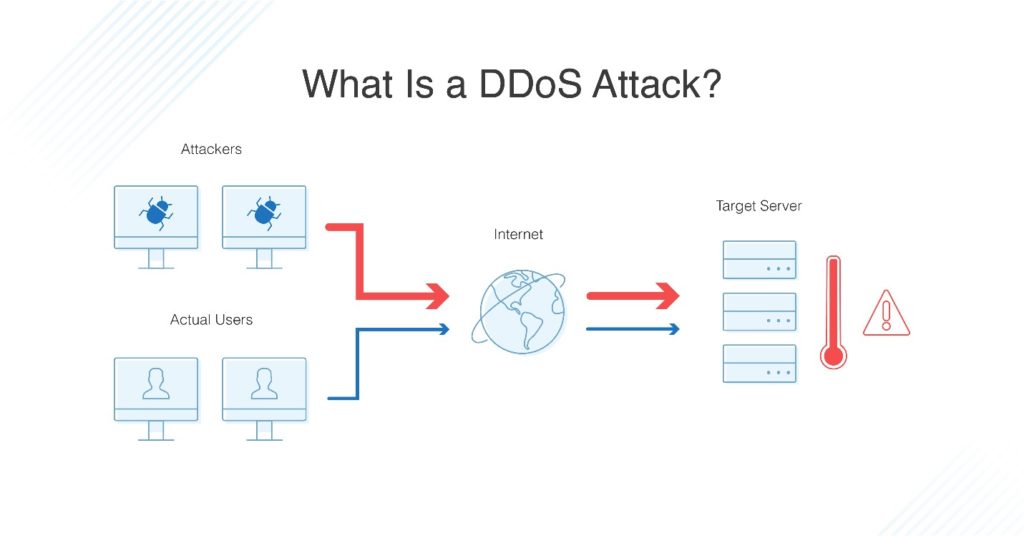
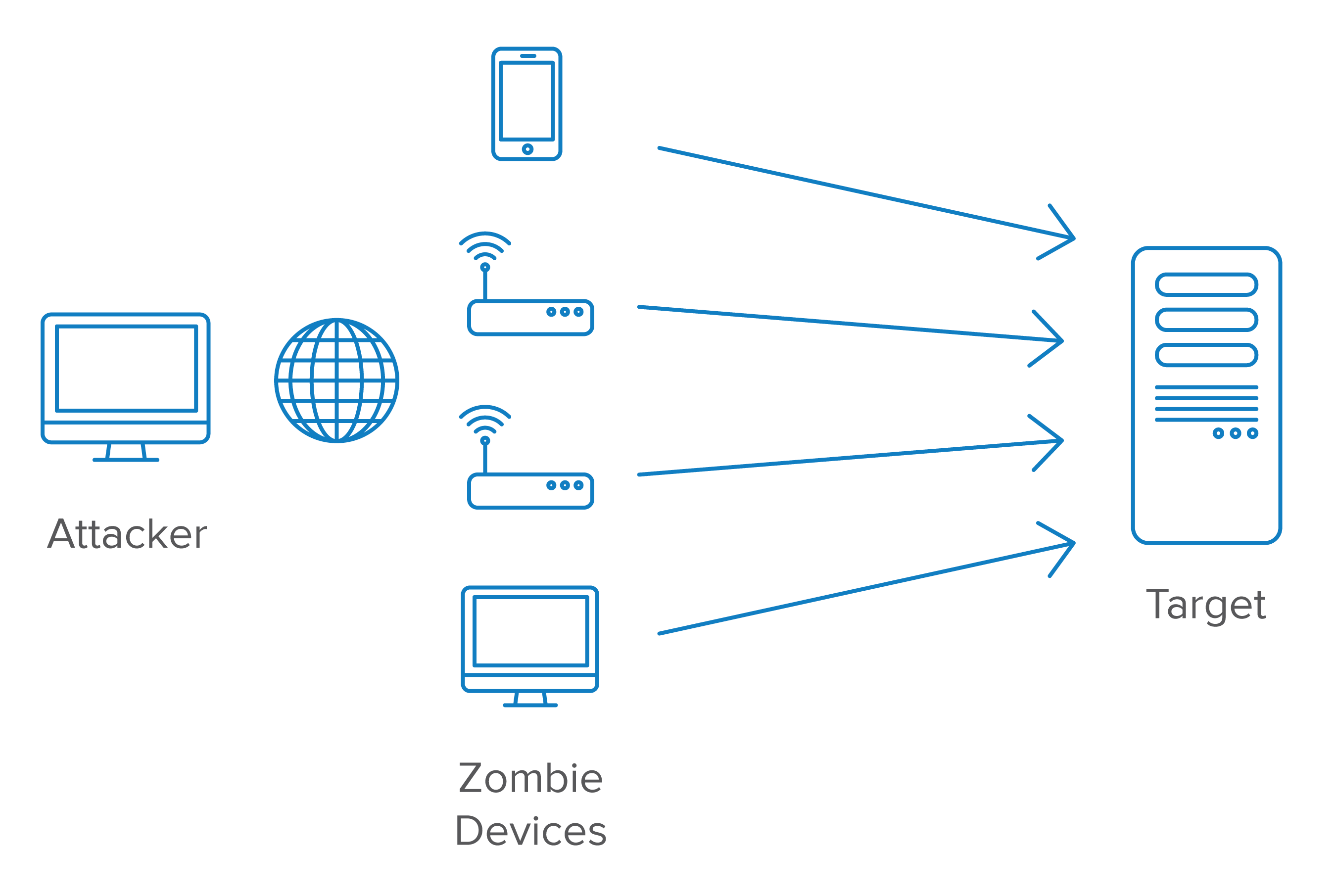
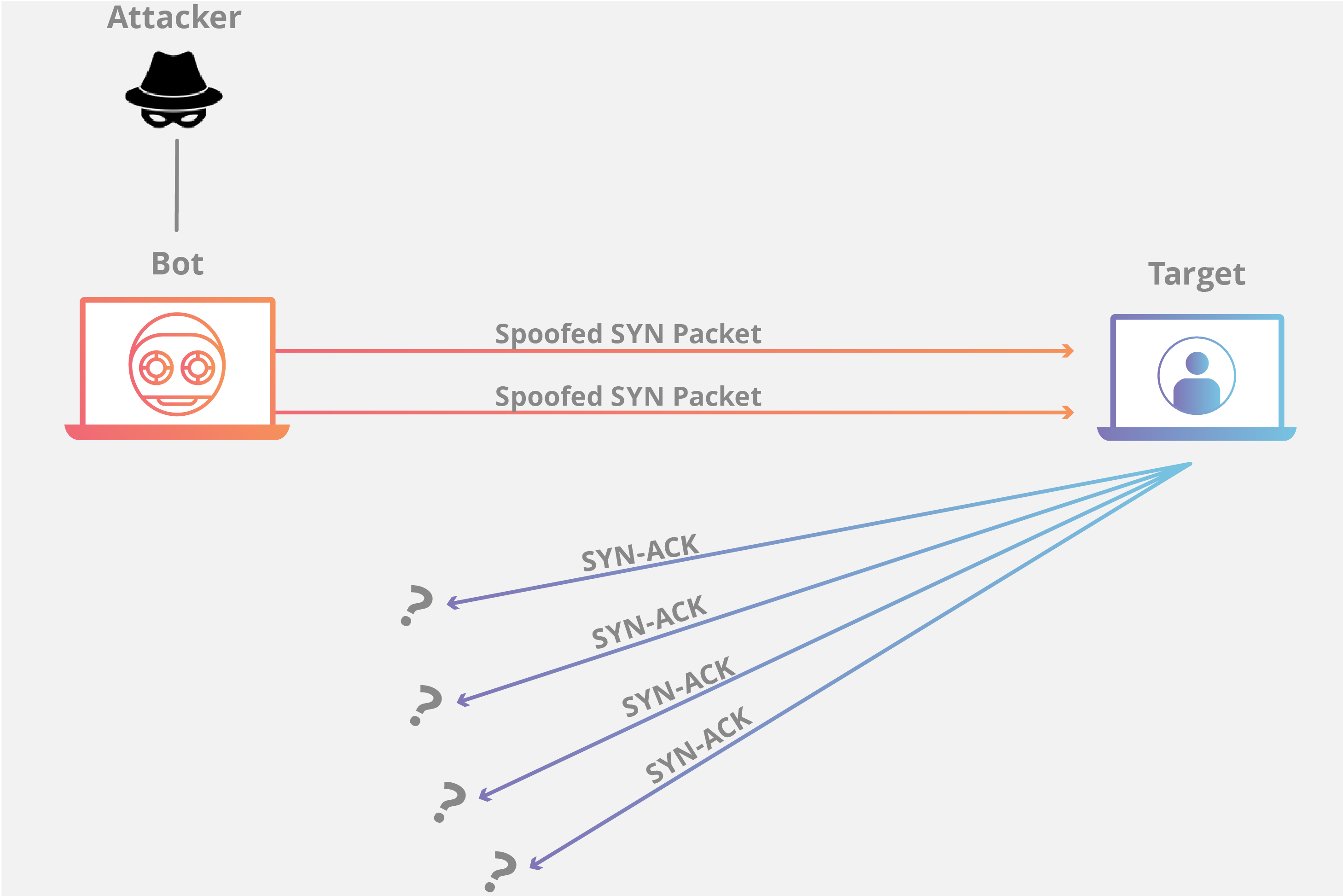
Train and educate your company on the potential impact of a ddos attack, know your “down time” tolerance, and rehearse with your staff your incident response and. Attacks such as syn flooding take advantage of bugs in the operating. A distributed denial of service attack (ddos) occurs when multiple systems flood the bandwidth or resources of a targeted system, usually one or more web servers.
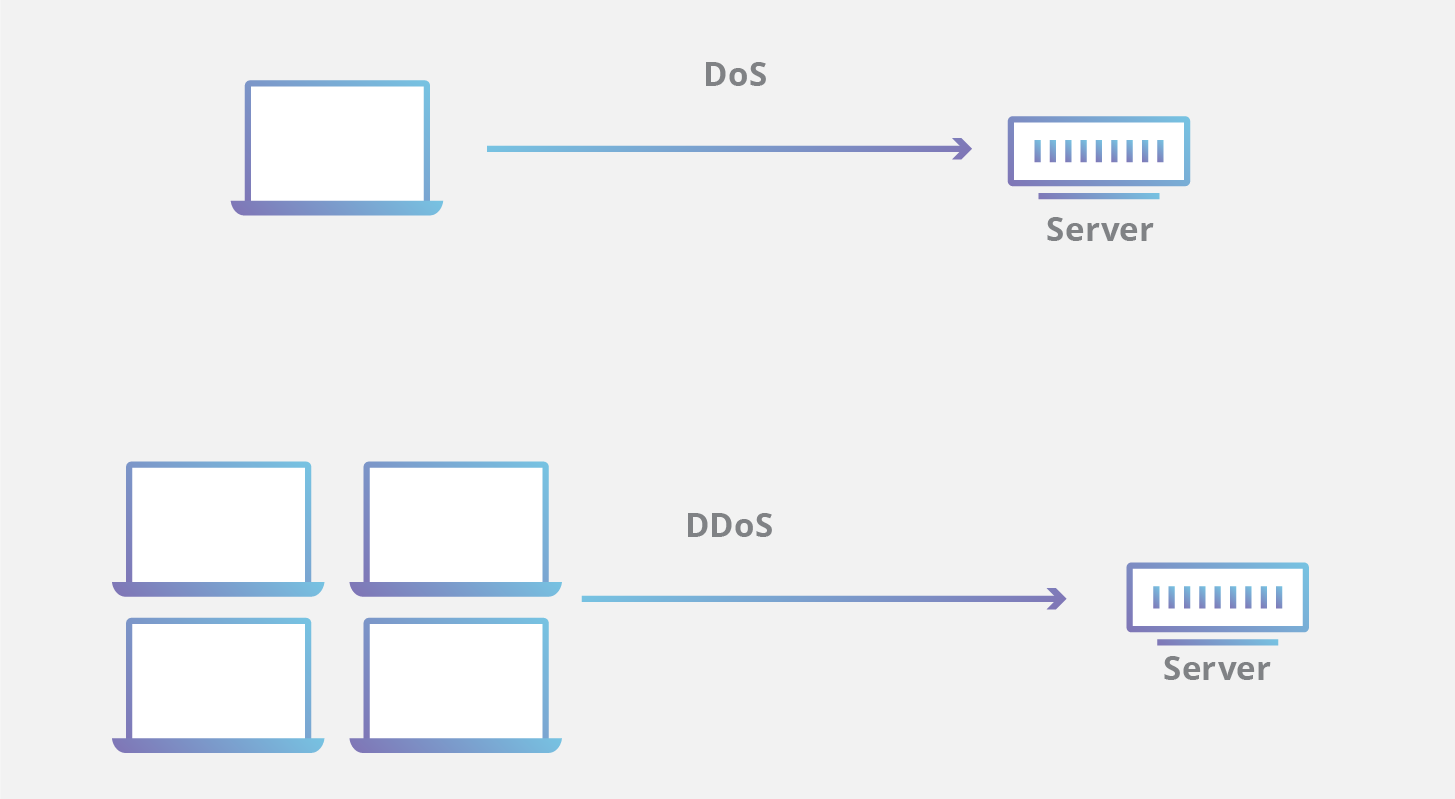
It is simple to write an application to do this and the consequences are far. Patch your infrastructure and installing new software versions, to. A dos is a denial of service attack, originating from a single machine that launches a barrage of network requests, overwhelming their target.
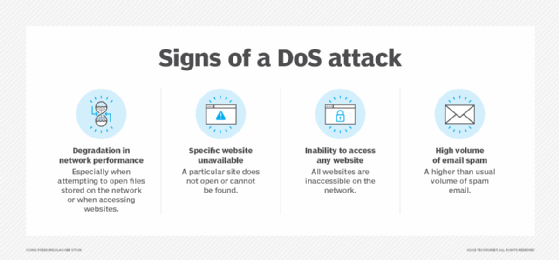
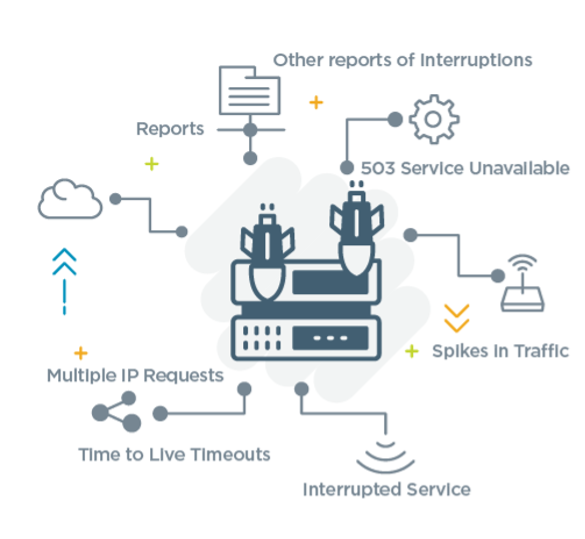
Refusing to talk about the problem one of the leading signs of denial is the. Protection against denial of service attacks. Outdated systems are usually the ones with most loopholes which denial of service attackers can find.
From the first known attack in 1999 to the highly publicized operation ababil, the. While dos attacks are less challenging to stop or prevent, ddos attacks can still present a serious threat. There are a number of.
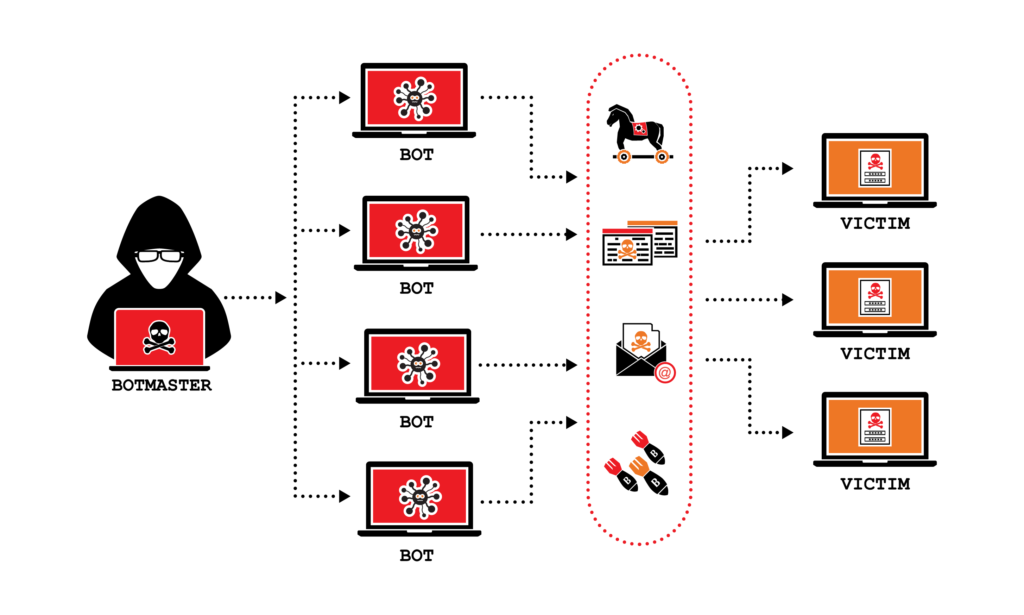
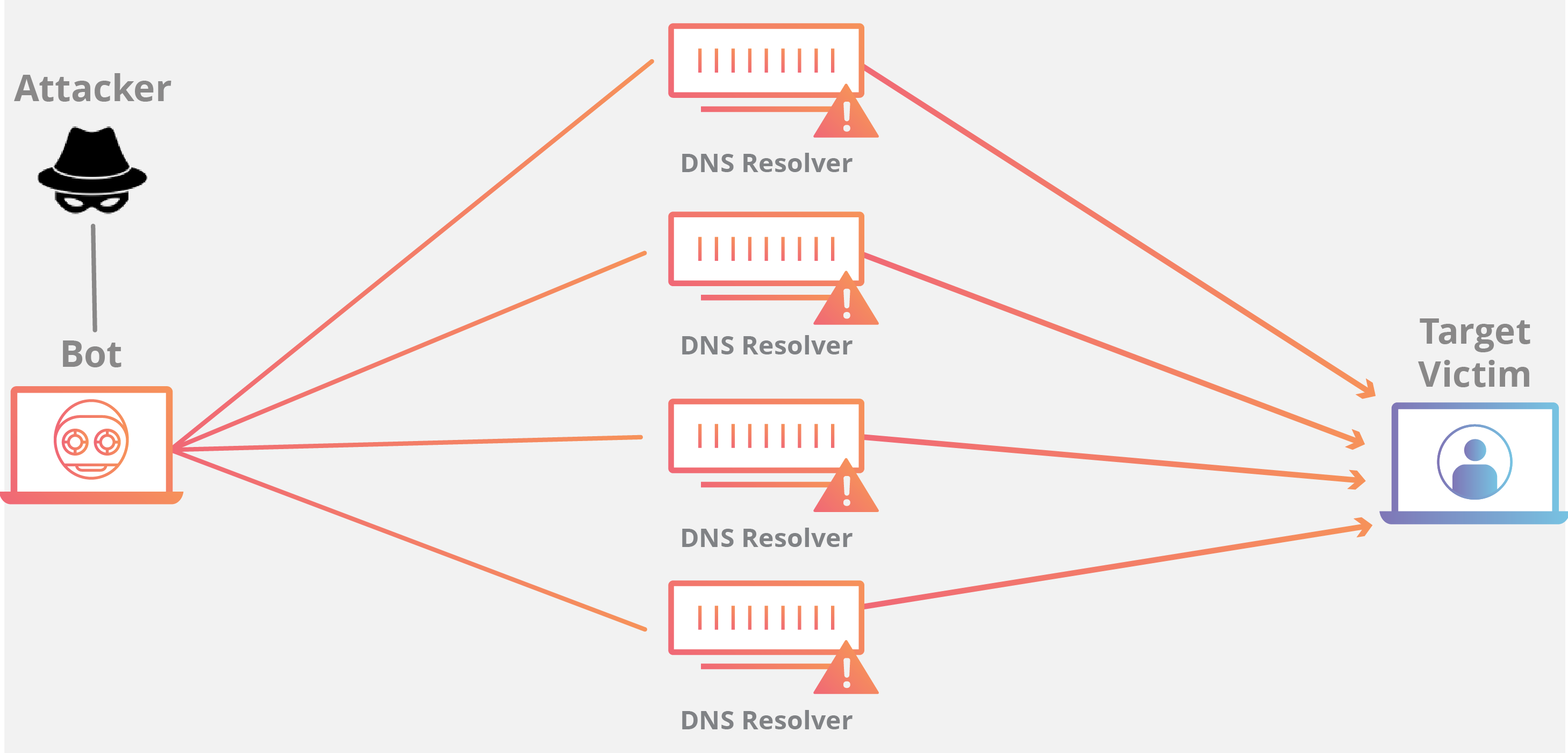
A denial of service attack (dos attack) is a type of cyberattack where the attacker tries to make a machine or network unavailable to its intended users. To know how to deal with someone in denial, you must be familiar with the following signs: A distributed denial of service (ddos) attack involves thousands of users generating.